The truth is that when you read about the latest data breach in the news or somewhere online, you probably don’t pay much attention to it. The only time it even blips on your radar is when significantly confidential information is hacked. Phishing attacks never cross your mind.
Social security numbers getting stolen or bank account numbers are the kind of information that makes you feel panicked. What you most likely don’t realize, is that what you think is harmless can actually be used to target a much more invasive.
Data leaks happen – there’s no stopping that. But you can protect yourself by knowing how scammers would use the data to access more personally identifiable information.

What Are Threat Actors And Why Do They Matter?
Looking at a phishing attack, scammers begin by sending an email that looks real but is actually fake. Criminals use reputable organization names and logos to try and trick users into clicking on an otherwise malicious ink.
By clicking on that link, the user may download a virus or other sort of malware. You may also unintentionally share personal information. Depending on what you have on your system, that data can include SSNs, credit card numbers, bank accounts, merchant logins, and any other info you think might be protected.
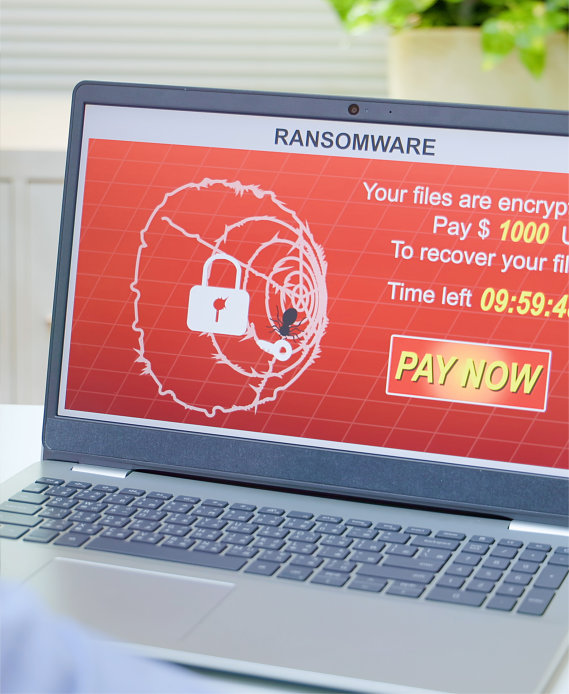
Ransomware Attack Payments Vs.
Non-Payment
The answer, in many cases, is to pay the ransom demand to get the business online sooner. Decisions tend to come from a place that can be emotional but also looks at the overall cost. Does it cost more to pay the ransom or to fight the attack?
One of the biggest issues is that many companies are simply not ready to deal with these attacks. Over the past several years, ransomware has affected hundreds of millions of employees, companies, and customers.
First, data goes through a systematic attack as ransomware encrypts files. Attackers then demand a ransom in bitcoin, to release the encryption and make the data available again.
In the end, IT pros are often left to deal with the chaos of bringing systems back online and resuming normal operations. The longer it takes to bring it all back online, the more money the company loses – in some cases, that amount could be millions. To further prevent the loss, companies feel pressured to simply pay the ransom to get back online fast.
When it works, criminals will gain access to your personal information and use it to cause all sorts of havoc ranging from opening fake accounts to shopping on your dime. Unfortunately, many don’t recognize what’s happening because they do such an effective job of copying the real site to a phishing website.
The next thing you know, you’re overdraft in your checking account or your savings is empty and you have no idea how. You can’t recall doing anything that may have been suspicious … but you kind of remember that one email you got about needing to reset your password that you never actually requested.

Preparing For a
Ransomware Attack
Best practices include updating employee access along with your network’s layout. That means making sure certain elements are in place like two-factor authentication, updating software, and providing training on security policies.
As you prepare for ransomware attacks, you also need to look at the current architecture, environment, and associated technology. Good questions to ask include:
- What weak points exist?
- Where are firewalls in place?
- How can an attack spread be reduced?
- Is there any separation between systems?
- Are there verified, working backups?
- How do employees impact the possibility of attacks?
It’s also important to note that people can also make mistakes by leaving passwords out in the open or their equipment unlocked when they leave. Intruders will then take advantage of those mistakes, and then they get into your systems.
To avoid an attack, you need to make sure your systems are built so the business doesn’t go down. That also means keeping backups updated and secured in an offline location. Additionally, you also want to ensure segment your systems on different networks to minimize damages.


Facing Ransomware Attacks
A well-thought-out approach can be the difference between allowing an attack to bring your entire organization down or being an annoying inconvenience. Having a plan or policy in place can prevent paying the ransom the attackers’ demands.
As it stands, most criminals are not based in-country and so are difficult to trace and persecute. Because of this challenge, it’s better to be prepared for an attack ahead of time. Get your house in order by protecting your systems so you are ready to go when and if attackers target your business. You will be grateful if it does.
To make sure you’re ready for a ransomware attack, IT Done For You can take a look at your systems and give you helpful tips. Contact us to learn more about what we can do for you and your business.

How Do You Recognize Real-World Phishing Attack Threats?
Scammers like to impersonate high-level authorities like government agencies. Think about it – those letters you get in the mail that look all official? You probably open them, and then after opening, realize that it’s all a ploy to get you to look.
Phishing attack emails do the same thing. They look like legitimate companies because they understand the psychological push that happens when you see something from a government entity. Anything that looks official might be a phishing attack in the making, so you need to verify its legitimacy.
To recognize these real-world threats, you never want to click on a link from an email in your inbox, especially if you didn’t ask for it. Instead, go out to the website and see if the claim in your email is real. You can also click on the “to” field in your email header to see what email address is coming from. If it looks off, it probably is and should just go into the trash.
How Can You Protect Against Phishing Attacks?
There are a few ways you can protect yourself from phishing schemes, too.
- Two-factor authentication on all of your online accounts
- Criminal marketplace scanning from an identity theft protection service
- Never click on a link or call a number found in an email
- Always go directly to the real website and call the number found there
- Filter out spam and phishing emails from your email inbox
- Hover your mouse without clicking on it over the link to verify where it’s going


Take Control of Your Identity Protection
Always do what you can to protect yourself. Once your data is out there, it’s too late to do much. Not to mention, it creates crazy headaches and hassles when you have to deal with the aftermath, especially in a business setting.
If you’d like some help or additional suggestions on how to protect your employee or customer identity information, contact IT Done For You. We’d be happy to schedule a consultation to help you ensure your security is top-notch.
Share This Story, Choose Your Platform!
Let’s have a 15-minute video call
We are now taking on new clients.





